Azure Policy Guest Configuration - Assignments
In the last part of this series around Azure Policy Guest Configuration, you got an introduction to what is Guest Configuration. In this part, you will learn about assigning Guest Configuration policies and initiatives.
Azure Policy Guest Configuration (GC) is an extension to Azure Policy and therefore use the same JSON definition structure. For example, here is the (redacted) GC definition for the policy Audit Windows machines that do not have the specified Windows PowerShell execution policy.
|
|
As you see in this definition, the overall document structure is same as an Azure Policy definition. However, the category in the metadata section at the top identifies this as a GC policy. This is a built-in GC policy definition.
Working with GC Policies
The following examples in this section use Azure CLI to work with GC policies. The az policy command helps you in working with policy definitions.
|
|
This command filters policy definitions to only GC policies and then returns JSON output containing only a few selected properties. Here is the sample output.
|
|
As you see in the output, you can see there are built-in and custom GC policies. The custom policies are what you as an end user can create and publish to your Azure subscription. Also, there are different modes – All and Indexed. The policies that are defined as all mode, the policy gets evaluated for all resource groups, subscriptions, and all resource types. When the policy is in indexed mode, it gets evaluated only for resources types that support tags and location.
To retrieve a single policy definition, you can use the az policy definition show command.
|
|
You can assign a GC policy using the az policy assignment command.
Note: There is a guestconfig extension that you can use to manage guest configuration assignments. However, I prefer az policy.
|
|
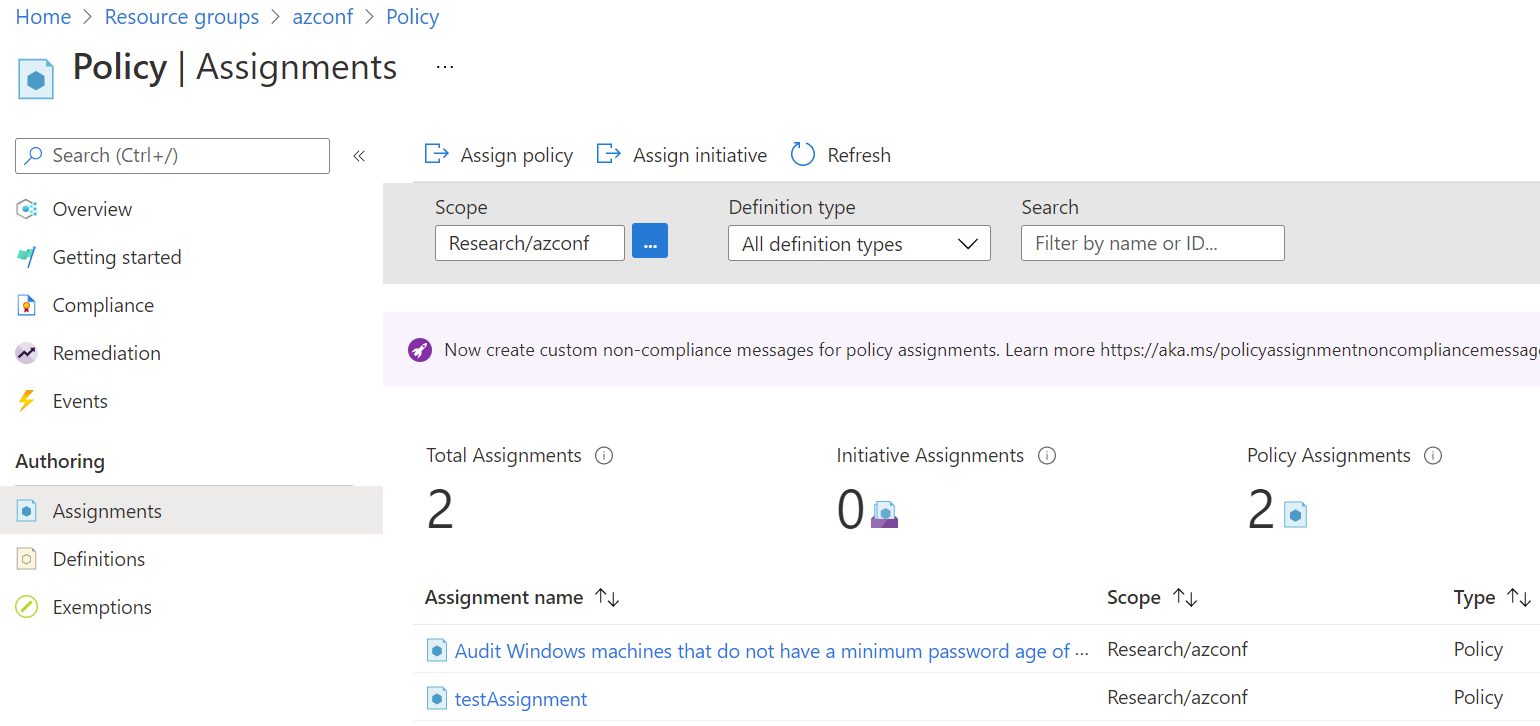
The argument to the --policy parameter is the value of name property you saw in the output of all policy definitions. Once this assignment is complete, you can see it in the portal.
You can trigger a policy compliance run using the az policy state command.
|
|
This will trigger the compliance run and wait for the task to return. If you do not want to block console until the task is complete, add --no-wait parameter.
You can check the policy assignment compliance state using the az policy state summarize command.
Working with GC initiatives
Initiatives are groups of policy definition. Initiatives help group related policy definitions and assign them at once to a Azure scope. You can list all available GC initiatives by running the following command.
|
|
This returns output similar to what is shown below.
|
|
You can now assign an GC initiative using the az policy assignment command and using --policy-set-definition parameter.
|
|
Checking the compliance state of an initiative assignment is similar to how you did that for policies.
This is all for today and in the next part of this series, you will learn about writing custom GC policies.
Share on: