Installing and Configuring Kubernetes cluster using kubeadm on Ubuntu
This article is more like a note to myself, but this may help if you are looking at configuring a Kubernetes cluster on Ubuntu.
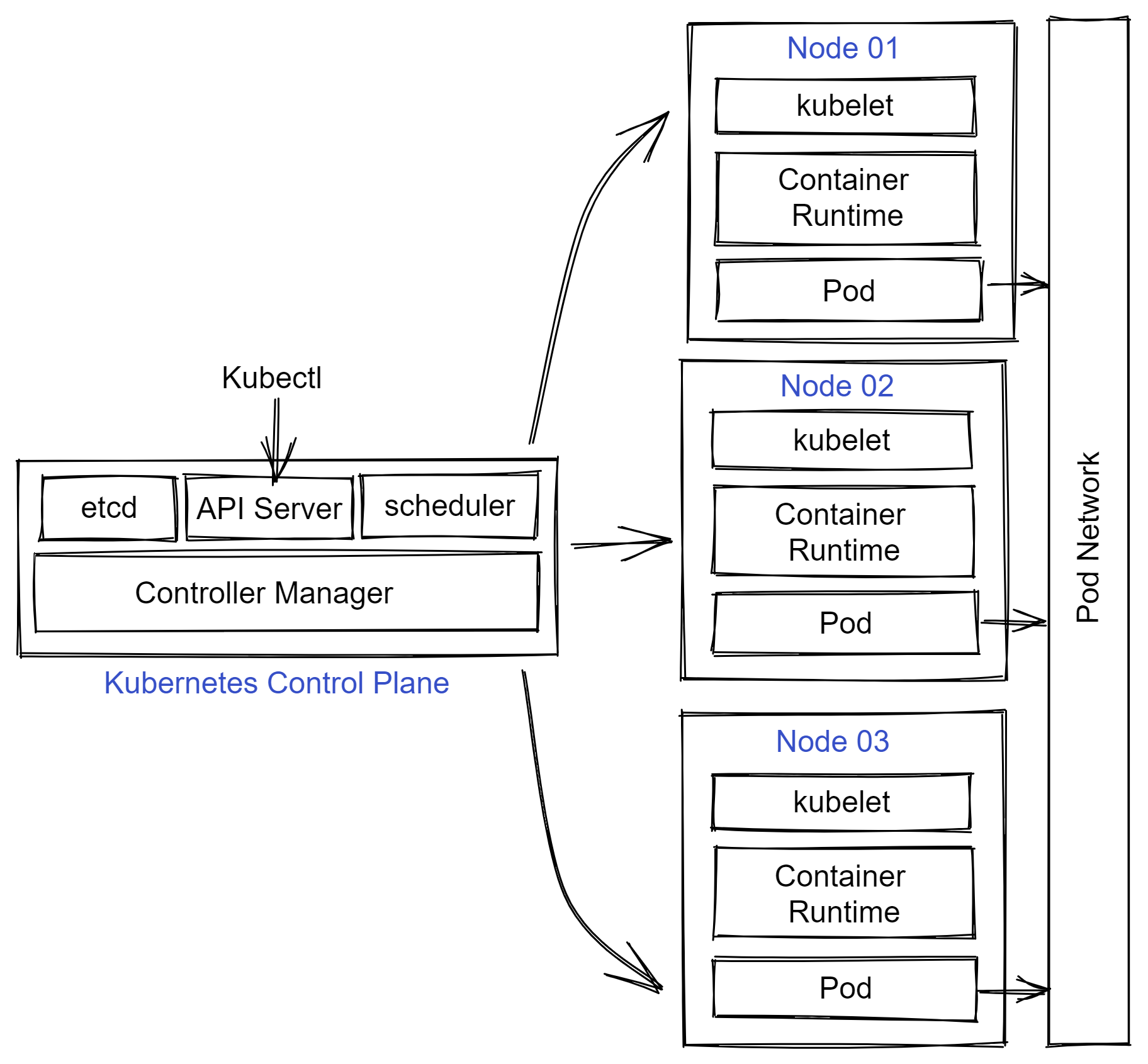
There are many ways to install and configure Kubernetes cluster for learning and development purposes. You can use Docker Desktop or Rancher Desktop or https://podman-desktop.io/ or minikube or microk8s to create a single node cluster for your development work quickly. I am a big fan of Docker Desktop and use that for any quick experiments. However, I need a multi-node cluster with additional services for anything more than simple deployment. I use Ubuntu virtual machines and configure a Kubernetes cluster using kubeadm.
In this article, I walk through the steps I followed to set up a virtual Kubernetes cluster.
Virtual machine configuration
To ensure I have enough resources in the cluster, I created four Ubuntu 22.04 LTS virtual machines on my Windows 11 system. Each of these VMs is configured with two virtual CPUs and 2GB of virtual memory. It is recommended to configure each virtual machine with a static IP address. I created an external virtual switch to enable Internet connectivity within the Ubuntu guest OS. Of the four virtual machines, I chose to use one as the control plane node and the other three as worker nodes.
Container runtime
Kubernetes uses a Container Runtime Interface (CRI) compliant container runtime to orchestrate containers in Pods.
Many runtimes are supported within Kubernetes. The most popular ones include Docker (via cri-dockerd), containerd, and CRI-O. The choice of a runtime depends on several factors, such as performance, isolation needs, and security. For this virtual cluster. I chose containerd as the runtime for my virtual cluster.
Container Network Interface (CNI)
Kubernetes requires a CNI-compatible Pod network addon for Pods within the cluster to communicate with each other. You can choose from many open-source and commercial CNI plugins to implement the Pod network. Once again, you need to consider factors such as ease of deployment, performance, security, and resource consumption to choose the Pod network addon that is correct for your Kubernetes cluster and the workload you plan to run.
I chose Calico as the pod network addon for the ease of deployment and considering the fact that I have some prior experience with Calico.
Preparing control plane and worker nodes
Each node in the Kubernetes cluster the following components.
- A container runtime
- Kubectl - The command line interface to Kubernetes API
- Kubelet - Agent on each node that receives work from the scheduler
- Kubeadm - Tool to automate deployment and configuration of a Kubernetes cluster
Before going into this, you must ensure that nodes that will be a part of the Kubernetes cluster can communicate with each other and the firewall ports required for node-to-node communication are open.
The following network ports must be open for inbound TCP traffic on the control plane node.
- 6443
- 2379:2380
- 10250
- 10257
- 10259
- 179 (required for Calico)
On the worker nodes, you should configure to allow incoming TCP traffic on the following ports.
- 10250
- 30000:32767
On Ubuntu, you can use ufw command to perform this configuration.
|
|
To see the bridged traffic, you must disable swap and configure IPv4 forwarding and IP tables on each node. Before all this, ensure each node has the latest and greatest packages. You will needcurl as well on the node to download certain packages.
|
|
You must disable swap on each node that will be a part of the Kubernetes cluster.
|
|
You must also check if the swap is listed in the /etc/fstab and either comment or remove the line.
Next, configure IPv4 forwarding and IP tables on each node.
|
|
Installing containerd
The next set of commands download the latest release of containerd from GitHub and configure it. You need to run this on each node.
|
|
Installing kubeadm, kubelet, and kubectl
These three tools are needed on each node.
|
|
The above commands download and install the three tools that we need on each node. Once installed, we mark the packages as held so that they don’t get automatically upgraded or removed.
Initialize Kubernetes cluster
Once the prerequisite configuration is complete, you can initialize the Kubernetes cluster using kubeadm init command.
|
|
This command starts a few preflight checks and the necessary Pods to start the Kubernetes control plane. At the end of successful execution, you will see output similar to what is shown here.
|
|
Before proceeding or clearing the screen output, copy the kubeadm join command. You need this to join the worker nodes to the Kubernetes cluster.
Prepare kube config
Before installing the Pod network addon, you need to make sure you prepare the kubectl config file. kubeadm init command provides the necessary commands to do this.
|
|
Once this is done, verify if the Kubernetes control plane objects can be queried or not.
|
|
This command will show only the control plane node and be shown as NotReady. This is because the Pod network is not ready. You can now install the Pod network addon.
Installing Calico
Installing Calico is just two steps. First, we install the opertor.
|
|
Next, we need to install the custom resources.
|
|
In this YAML, you need to modify the the spec.calicoNetwork.ipPools.cidr to match what you specified as the argument to --pod-network-cidr. Once this modification is complete, you can implement the custom resources.
|
|
You need to wait for the Calico Pods to transition to Ready state before you can proceed towards joining the worker nodes to the cluster.
|
|
Once all Calico pods in the calico-system namespace are online and ready, you can check if the control plane node is in ready state or not using kubectl get nodes command.
Finally, you can move on to joining all worker nodes the cluster. You need to run the command you copied from the kubeadm init command on each worker node.
|
|
Note: IP, token, and hash in the command you copied will be different.
The node joining process takes a few minutes. On the control plane node, you can run watch kubectl get nodes command wait until all nodes come online and transition to ready state.
|
|
You should also verify if all control plane pods are online and ready or not.
|
|
This is it. You now have a four node Kubernetes cluster that you can use for your learning, development, and even production (if you are brave enough!).
Share on: